Software Testing Techniques – 3
Performance Testing
Performance testing assists in identifying performance bottlenecks, optimizing system performance, and improving user experience by analyzing system performance characteristics under certain workload conditions. It ensures whether the performance standards are satisfied by testing and evaluating the system’s responsiveness, stability, scalability, and resource utilization.
What are the types of Performance Testing?
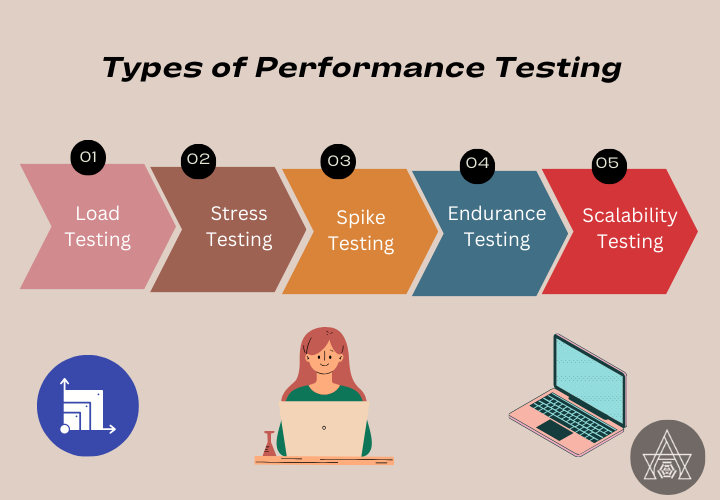
- Load Testing: Assesses the system’s performance under expected user loads to ensure it can handle the demand.
- Stress Testing: Extends the system’s behavior and stability beyond its typical operational boundaries.
- Spike Testing: Determines the system’s ability to handle unexpected increases in user traffic or workload.
- Endurance Testing: Validates the system’s performance and stability over a long period of time to determine its long-term viability under sustained loads.
- Scalability Testing: Assesses the system’s capacity to scale up or down in response to changing workload demands.
What are the key steps in the process of Performance Testing?
- Clearly define the performance goals and metrics to be measured during testing.
- Select appropriate testing tools and create a test environment that closely resembles the production environment.
- Design realistic test scenarios and identify representative data sets to simulate real-world usage patterns.
- Execute the performance tests, record relevant performance metrics, and monitor the system behavior.
- Analyze the collected data, identify performance bottlenecks, and generate comprehensive reports highlighting the findings and recommendations for improvement.
What are the key metrics of Performance Testing?
- Response Time: The time it takes the system to react to user queries.
- Throughput: The number of transactions or requests processed by the system in a given amount of time.
- Resource Utilization: Assesses the system’s utilization of CPU, memory, network, and other resources.
- Error Rate: Determines the frequency with which errors occur during the performance test.
- System Availability: Measures the uptime and availability of the system during the test.
- User Concurrency and Virtual User Load: Evaluates the system’s performance when numerous concurrent users and different virtual user loads are present.
What are the best practices that need to be followed when conducting Performance Testing?
- Test frequently and early in the development cycle to discover and address performance issues.
- Use realistic load and test data that closely resemble actual usage scenarios.
- During tests, monitor system performance to gain real-time insights and identify bottlenecks.
- Analyze test data to detect performance issues, uncover root causes, and make educated optimization decisions.
- Include developers and operations teams in performance testing to encourage collaboration and to align efforts to improve system performance.
What are the tools and technologies used in Performance Testing?
- Open-source tools: JMeter, Gatling, Locust
- Commercial tools: NeoLoad, Silk Performer, LoadRunner

The selection of a specific tool depends on factors such as project requirements, budget, technical expertise, and the complexity of the performance testing scenarios.
What is Cloud-based Performance Testing?
The technique of conducting performance testing activities using cloud computing resources and infrastructure is referred to as cloud-based performance testing.
In cloud-based performance testing, the load generation and test execution processes are carried out in the cloud environment instead of relying solely on in-house technology. This approach offers several advantages:
- Scalability: Cloud systems allow you to scale resources up or down dependent on your testing needs. This enables testers to mimic large-scale user demands and assess system performance in various circumstances.
- Cost-effectiveness: Cloud-based performance testing reduces the need for organizations to invest in and maintain discrete hardware infrastructure.
- Accessibility: Cloud-based performance testing allows testers to run tests from any location with internet connectivity.
Popular cloud-based performance testing tools include:
- BlazeMeter
- LoadView
- Flood IO

What are the challenges encountered when conducting Performance Testing?
- Without careful planning and preparation, insufficient test coverage and erroneous findings may occur.
- It is difficult to simulate the different user behaviors and system usage patterns observed in real-world contexts.
- Due to time and resource constraints, the scope of performance testing may be limited, perhaps leaving certain aspects untested.
- It is critical to protect sensitive information and maintain data security and privacy throughout performance testing.
What are the benefits of Performance Testing?
- Assess release readiness
- Improve the efficiency
- Measure the adequacy of application performance
- Eliminate avoidable system tuning efforts
- Evaluate infrastructure adequacy
- Identify mismatches between performance related expectation and reality
Performance testing is crucial in ensuring that software applications run optimally under a variety of scenarios. Organizations can discover performance concerns early, optimize system performance, and provide high-quality applications that exceed user expectations by adopting best practices, leveraging suitable tools, and addressing challenges.
Security Testing
Organizations can reduce risks, protect sensitive information, and improve the trustworthiness of their software applications by doing security testing.

What are the types of Security Testing?
| Security Testing Type | Purpose | When to Use |
| Penetration Testing | To identify vulnerabilities by simulating real-world attacks and attempting to exploit them. | • When a comprehensive evaluation of system security is needed. • After implementing security measures to assess their effectiveness. • To identify potential entry points for attackers and evaluate the impact of successful attacks. |
| Vulnerability Testing | To identify specific vulnerabilities in a system or application. | • As a routine part of the software development life cycle (SDLC) to identify and fix vulnerabilities early on. • When a new system or application is deployed or updated. • To comply with security regulations or industry standards. |
| Risk Assessment | To assess and prioritize security risks based on their potential impact and likelihood of occurrence. | • Before implementing security measures to determine the most critical areas to focus on. • When making strategic decisions regarding security investments and resource allocation. • To understand the overall risk landscape and guide risk mitigation efforts. |
What are some common Security Threats?
- Cross-site scripting (XSS): Manipulates web application vulnerabilities to inject malicious scripts.
- Buffer overflow attacks: Aim to overwhelm a system’s memory by exceeding its allocated space.
- Distributed Denial of Service (DDoS) attacks: Overwhelm a target system or network with an excessive volume of requests, rendering it unavailable to legitimate users.
- Phishing: Uses deceptive emails, messages, or websites to trick users into revealing sensitive information such as passwords, credit card numbers, or personal data.
- Pharming: Redirects website traffic to a malicious site by tampering with DNS settings or using other means to alter the destination IP address.
What are the tools used in Security Testing?
- Burp Suite is a popular tool for web application security testing, facilitating tasks such as scanning for vulnerabilities and analyzing network traffic.
- Metasploit is an extensive framework for penetration testing and vulnerability assessment, offering a wide range of exploit modules.
- Nmap is a versatile network scanning tool that helps identify open ports, detect potential vulnerabilities, and map network architecture.
What are the best practices that need to be followed when conducting Security Testing?
- Establishing a comprehensive security testing methodology to ensure that the testing process is well-defined, consistent, and aligned with industry standards and best practices.
- Prioritizing testing efforts to identify critical assets, potential threats, and vulnerabilities that require immediate attention.
- Documenting findings and maintaining a repository of security test results for effective analysis, tracking of remediation efforts, and sharing of valuable insights across the organization.
How to carryout test reporting and communication during Security Testing?
Effectively communicating security test findings and results to stakeholders is essential for driving action and ensuring that necessary security measures are implemented. It is crucial to provide concise and understandable reports that highlight identified vulnerabilities, their potential impact, and recommended mitigation strategies. Communicating with both technical and non-technical stakeholders requires tailoring the message to the appropriate audience, emphasizing the business impact and the importance of security measures in protecting sensitive information.
What are the regulatory requirements of Security Testing?
Organizations must adhere to standards such as:
- Payment Card Industry Data Security Standard (PCI-DSS)
- Health Insurance Portability and Accountability Act (HIPAA)
- General Data Protection Regulation (GDPR)
What is the role of Security Testing in DevOps:
- Early Vulnerability Detection: Integrating security testing into DevOps pipelines allows for the early detection of vulnerabilities and security weaknesses in software applications. This proactive approach helps identify and address potential security issues before they are deployed to production.
- Continuous Security Assurance: Security testing becomes an integral part of the continuous integration and delivery process, ensuring that security measures are consistently validated at each stage of the software development life cycle. This ongoing security assurance helps maintain the security posture of the application throughout its lifecycle.
- Automation and Tooling: DevOps enables the automation of security testing processes, making use of specialized security testing tools. Automation reduces human errors and ensures that security testing is executed consistently and efficiently across different environments and deployments.
- Collaboration and Shared Responsibility: Security testing in DevOps fosters collaboration and shared responsibility among development, operations, and security teams. By involving security experts early in the development process, organizations can address security concerns and make informed decisions about risk mitigation strategies.
- Compliance and Risk Management: Security testing in DevOps helps organizations comply with industry regulations and standards by continuously monitoring and assessing the security of their applications. It allows for the identification and mitigation of security risks, reducing the potential impact of security breaches.
- Building User Trust: By integrating security testing practices, organizations demonstrate their commitment to building secure and reliable software products. This builds trust with users and stakeholders, enhancing the reputation of the organization and its products in the market.
- Secure Deployment: Security testing in DevOps ensures that software applications are thoroughly tested for security vulnerabilities before being deployed. This reduces the risk of introducing security weaknesses into the production environment and helps deliver robust and secure software products to end-users.







I do not even know how I ended up here but I thought this post was great I dont know who you are but definitely youre going to a famous blogger if you arent already Cheers.
I love how this blog celebrates diversity and inclusivity It’s a reminder that we are all unique and should embrace our differences