Software Testing Techniques – 4
Boundary Value Analysis
Functional testing is a common software testing methodology that aims to assess the extent to which a software system corresponds to its functional requirements. This type of testing is primarily concerned with verifying that the system’s features and functions operate as intended and that they meet the specified business requirements. By conducting functional testing, software testers can identify and report any defects or issues that may impact the system’s functionality, usability, and overall quality. This approach to testing is critical to ensuring that software systems are reliable, efficient, and effective in meeting the needs of their users. The primary objective of this undertaking is to conduct a comprehensive evaluation of the application’s functionality and ascertain that it adequately satisfies the predetermined requirements.
Functional testing is a crucial software testing technique that is designed to verify whether each function of a software application performs in compliance with the predetermined requirements and specifications. This type of testing is performed to ensure that the software application is functioning as intended and that it meets the user’s expectations. The primary objective of functional testing is to identify any defects or issues that may arise during the software development process and to rectify them before the software is released to the end users. By conducting functional testing, software developers can ensure that the software application is reliable, efficient, and user-friendly. Boundary Value Analysis (BVA) is a software testing technique that falls under the category of functional testing. It involves evaluating the behavior of a system at the boundaries of its input domain. The objective of BVA is to identify any defects or errors that may arise due to the system’s inability to handle inputs that are at or near the limits of its input.
Boundary Value Analysis is a testing methodology that involves a comprehensive review of the boundary values that are associated with both valid and invalid partitions. This approach works towards ensuring that the system being tested is able to handle inputs that are at the limits of its acceptable range. By examining the boundary values, testers are able to identify potential issues that may arise when the system is subjected to extreme inputs. This methodology is particularly useful in ensuring that the system is robust and can handle a wide range of inputs without experiencing any adverse effects. It has been observed that the probability of erroneous conduct tends to escalate towards the periphery of the equivalence partition, in contrast to the occurrences within the confines of the partition. The identification of defects through testing is more probable in the critical area of boundaries.
In the context of algorithmic processes, it is common practice to implement a verification mechanism that specifically targets input values that are situated in close proximity to the boundary of the input domain. This approach is motivated by the fact that such values are more susceptible to errors due to a variety of factors, including but not limited to numerical instability, rounding errors, and precision limitations. Therefore, by focusing on the verification of boundary values, the algorithm in the realm of mathematical analysis, it is customary to define a partition as a collection of non-empty, mutually disjoint intervals, each of which is characterized by its upper and lower limits, which serve as the partition’s boundaries. This definition is widely accepted and utilized in various mathematical contexts, as it provides a clear and concise means of describing the structure and properties of partitions.
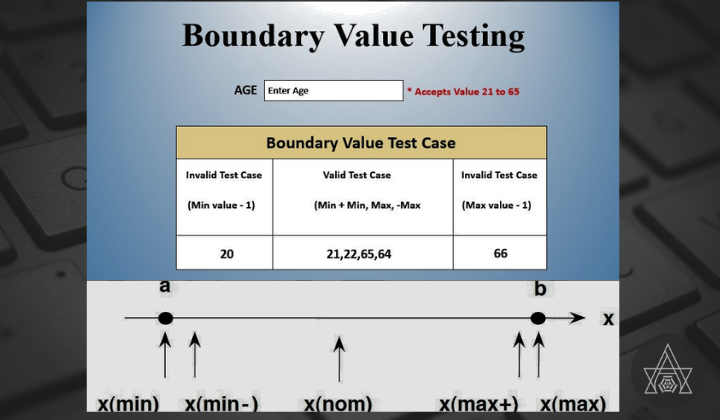
For each variable we check-
- Minimum value.
- Just above the minimum.
- Nominal Value.
- Just below Max value.
- Max value.
Summary of Boundary Value Analysis,
Use for
The input data values are compared to the boundaries that have been specified by BVA.
Testing Values
The input test data values encompass the minimum value plus one, the minimum value, the minimum value minus one, the nominal value, the maximum value plus one, the maximum value, and the maximum value minus one.
Bug Identification
Only errors that occur at boundary values are found by it.
Application Areas
It is a component of both the stress test and the negative test.
Usage Condition
Applications with close boundary values are the only ones that can utilize it.
Equivalence Partitioning
It is a form of black box testing that may be utilized for the testing of software at any level. Using this approach, the input data are first partitioned into equivalent subsets, which are then used in the process of building test cases.
The process involves the partitioning of input data into distinct equivalence data classes, each of which shares common characteristics or behaviors. The concept finds its application in scenarios where there exists a spectrum of potential input values.
The following are the guidelines for applying Equivalence Partitioning:
- When the range condition is provided as an input, it establishes one acceptable equivalence class and two invalid ones.
- When a particular value is provided as an input, a single acceptable equivalence class is established alongside two invalid ones.
- When an input member of a set is provided, two equivalence classes are generated, one valid and one invalid.
- When a Boolean value is provided as an input condition, it results in the establishment of a valid and an invalid equivalence class.
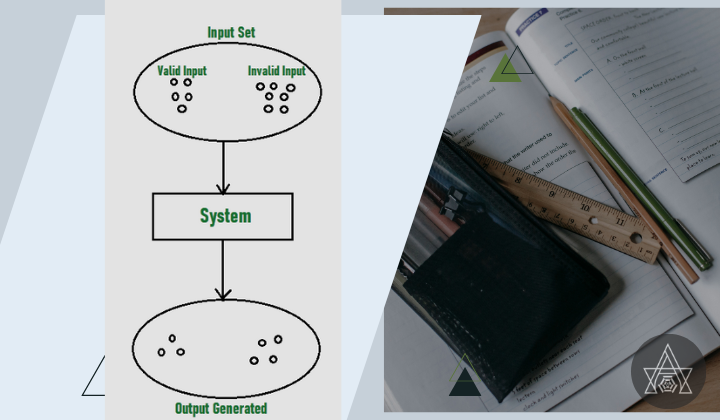
Summary of Equivalence Partitioning,
Use for
The Equivalence Partitioning algorithm looks at the values of the input data from a range that covers the equivalence class intervals.
Testing Values
Equivalence partitioning is a software testing methodology that entails the identification of valid and invalid ranges of equivalence classes for the purpose of testing developed applications.
Bug Identification
It is helpful in locating flaws in the partitioned equivalence data class in between the partitions.
Application Areas
It is possible to carry it out at any step of the software testing process, including the unit testing stage.
Usage Condition
The Appropriateness of Equivalence The accuracy with which the tester recognizes the equivalence class is directly proportional to the success of the partitioning process.
Decision Table Testing
Decision tables are commonly used in various engineering disciplines to depict intricate logical connections. Software testing is a highly effective technique for evaluating software and the implementation of requirements. The resultant output is contingent upon numerous input conditions, and decision tables present a tabulated perspective of diverse permutations of input conditions, which are expressed as True (T) and False (F). Moreover, it furnishes a series of stipulations and their corresponding measures necessary for the testing process.
Parts of Decision Tables:

In software testing, the decision table is constructed into 4 parts, which are divided into the following:
- Condition Stubs: The initial set of criteria is presented in the top-left quadrant of the decision table, which serves as a tool for selecting a course of action or multiple courses of action.
- Action Stubs: All the possible actions are listed in the first lower left part of the decision table, which is below the condition stub.
- Condition Entries: In the decision table, the values for the condition entries go in the top right corner. In the condition values part of the table, there are multiple rows and columns, which are called Rules.
- Action Entries: Each entry in the action entry has an action or set of actions in the lower right corner of the decision table. These numbers are called outputs.
Different kinds of decision tables:
There are two types of choice tables, which are listed below:
Limited Entry: In limited entry decision tables, you can only put in binary numbers for the conditions.
Extended Entry: The condition entries in the extended entry decision table have more than two numbers. Extended entry decision tables are tables that use more than two conditions. If a condition can be more than just “true” or “false,” they are called “extended.”
How Decision Tables Can Be Used:
- The action that is taken is not affected by the order in which rules are evaluated.
- Only at the unit level is it easy to use the choice tables.
- Once a rule is met and an action is chosen, another rule must be looked at.
- Few tools can’t be used because of the rules.
Exploratory Testing
It Exploratory Testing involves simultaneous learning, test design, and execution, making it effective for uncovering defects and understanding complex systems.
This is a mode of testing which is unscripted and allows testers to actively explore the system, making real-time decisions based on their observations. It encourages creativity, critical thinking, and adopting the end-user’s perspective. Unlike scripted testing, it offers flexibility to adapt the approach based on emerging information.
Principles of exploratory testing:
- Context-Driven Approach: Testers adapt their approach to the specific context, focusing on critical areas and adjusting techniques accordingly.
- Simultaneous Learning and Testing: Exploratory testing combines learning and testing, refining strategies, and test cases iteratively.
- Charter-Based Testing: Testers use charters to guide their sessions, defining scope, objectives, and areas of focus.
Benefits of exploratory testing:
- Uncovering Complex Defects: Testers uncover defects that scripted testing might miss. They simulate real-world scenarios, identify edge cases, and discover unexpected behaviors.
- Validating Usability and User Experience: Exploratory testing focuses on the user’s perspective, uncovering usability issues and inconsistencies.
- Agile and Rapid Feedback: Exploratory testing complements agile development by providing timely feedback on software quality.
- Effective Bug Advocacy: Testers articulate findings and observations effectively, helping developers understand and reproduce issues.
Best practices for exploratory testing:
- Test Session Preparation: Spend time understanding the system, defining objectives, and establishing a testing charter.
- Test Design Techniques: Utilize various techniques like boundary value analysis and equivalence partitioning to guide exploration and ensure coverage.
- Note-Taking and Documentation: Maintain thorough notes to capture observations, defects, and ideas for further testing.
- Collaboration and Knowledge Sharing: Engage in collaboration and knowledge sharing to enhance the testing process.
- Continuous Learning and Improvement: Reflect on past sessions, identify areas for improvement, and incorporate lessons learned.
By actively exploring the system, testers uncover complex defects, validate usability, and provide rapid feedback. Adhering to the principles and best practices of exploratory testing maximizes its benefits, improving software quality.
State Transition Testing
State transition testing is a widely used software testing technique aiming to analyze a system’s behavior as it transitions between different states. This methodology is particularly effective in scenarios where the system being tested has discrete states, and its behavior is dependent on the current state and the input received.
In the context of software systems, a state represents a specific condition or mode in which the system exists. This could manifest as a particular screen or page, a specific configuration, or any other distinct state that is relevant to the system’s functionality. Transitions, on the other hand, refer to the movement or alteration from one state to another, often triggered by specific events or inputs. By closely examining the behavior of the system during these transitions, testers gain valuable insights into its functionality and potential defects.
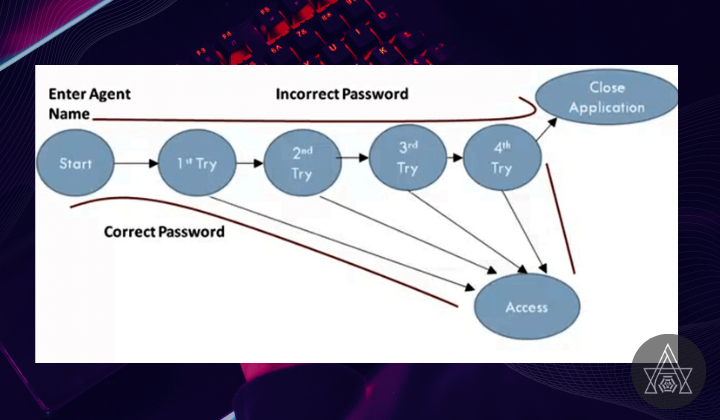
Key Concepts in State Transition Testing:
State transition testing involves several key concepts that aid in designing and executing effective test scenarios. These concepts include:
- States and Events: Testers identify and define the different states the system can assume during its operation. They also identify events or inputs that trigger transitions between these states. This understanding forms the basis for creating test cases that cover various combinations of states and events.
- Transition Coverage: The goal of state transition testing is to achieve thorough coverage of state transitions. Testers aim to test all possible valid and invalid transitions within the system. By ensuring comprehensive transition coverage, potential defects arising from state changes can be effectively identified and resolved.
- Transition Conditions and Actions: Each state transition is associated with specific conditions and actions. Conditions define the requirements that must be met for the transition to occur, while actions describe the behavior or changes that take place during the transition. Test cases are designed to verify that the system behaves correctly in response to these conditions and actions.
Benefits of State Transition Testing
State transition testing offers several benefits that contribute to the overall quality and reliability of software systems. These advantages include:
- Improved Test Coverage: By focusing on transitions between states, state transition testing provides comprehensive coverage of the system’s behavior. It ensures that all relevant states and their associated transitions are thoroughly tested, increasing the chances of detecting defects and anomalies.
- Identification of Boundary Conditions: State transitions often involve boundary conditions where the system behavior may differ. By specifically targeting these transitions, state transition testing helps identify and validate the system’s behavior in critical edge cases, reducing the risk of errors and failures.
- Early Detection of Defects: As state transition testing explores the behavior of the system during transitions, it enables early detection of defects related to state changes. By verifying that the system responds correctly to events and inputs during transitions, potential issues can be identified and addressed at an early stage, leading to improved software quality.
- Enhanced Test Maintainability: State transition testing promotes modular and reusable test cases. As transitions and their associated conditions and actions are clearly defined, test cases can be easily adapted and reused when changes occur in the system. This improves test maintainability and reduces the effort required for regression testing.
- Increased Test Efficiency: State transition testing allows testers to focus on critical transitions and prioritize their testing efforts accordingly. By selecting relevant test cases that cover a wide range of transitions, testing efficiency is enhanced, ensuring that resources are utilized optimally.
Best Practices for State Transition Testing
To maximize the effectiveness of state transition testing, certain best practices should be followed:
- Define and Document States and Transitions: Clearly define the states and transitions within the system, documenting them comprehensively. This serves as a reference for test case design and ensures a shared understanding among testers.
- Prioritize Test Scenarios: Identify and prioritize test scenarios based on the significance and frequency of state transitions. Focus on critical transitions and prioritize the testing effort accordingly to achieve maximum coverage and risk mitigation.
- Cover Valid and Invalid Transitions: Design test cases to cover both valid and invalid transitions. Valid transitions ensure the system behaves correctly when moving between valid states, while invalid transitions verify that the system handles unexpected or erroneous inputs appropriately.
- Consider Boundary Conditions: Pay special attention to boundary conditions during state transitions. Test cases should cover scenarios where the system is on the edge of transitioning to a different state, ensuring its behavior remains consistent and accurate.
- Use Combinatorial Testing Techniques: Employ combinatorial testing techniques, such as pairwise or orthogonal array testing, to generate an optimal set of test cases. This approach helps achieve high coverage while minimizing the number of test cases required.
State transition testing is a valuable technique in software testing, allowing testers to examine the behavior of systems as they transition between different states. By focusing on transitions, verifying conditions and actions, and achieving comprehensive coverage, state transition testing aids in the identification of defects, validation of correct behavior, and enhancement of overall software quality. By adhering to best practices and leveraging automation, testers can effectively design and execute state transition tests, ensuring robust and reliable software applications
Conclusion
In conclusion, these testing techniques each play a crucial role in ensuring the quality, performance, security, and usability of software systems.
Usability testing and exploratory testing are vital for gaining insights into user experience and identifying any usability issues that may arise. By observing how users interact with the system, usability testing helps designers and developers make informed improvements to enhance overall user satisfaction.
Performance testing is essential to verify that the system can handle various workloads without any significant degradation in performance. By simulating real-world scenarios and measuring factors such as response time, throughput, and resource utilization, performance testing ensures that the system meets performance expectations and can scale effectively as the user load increases.
Security testing is of utmost importance to protect sensitive data and prevent unauthorized access. By conducting thorough security assessments, including penetration testing and vulnerability scanning, any potential vulnerabilities or weaknesses in the system can be identified and addressed. This helps safeguard the system from potential attacks and ensures compliance with industry standards and regulations.
Boundary value analysis and equivalence partitioning are techniques that optimize test coverage while efficiently uncovering defects. Boundary value analysis focuses on testing the behavior of the system at the edges of input ranges, where defects are more likely to occur. Equivalence partitioning groups inputs into partitions that are expected to exhibit similar behavior, allowing for representative test case selection. By employing these techniques, testers can target critical areas of the system and ensure comprehensive coverage while minimizing redundant test cases.
Decision table testing plays a significant role in validating complex business rules and logic within a system. By creating a table that maps various combinations of inputs to expected outputs based on defined rules, decision table testing ensures that all combinations are thoroughly tested. This technique verifies that the system’s decision-making capabilities are accurate, reliable, and in line with the specified business rules.
Lastly, exploratory testing allows testers to exercise their expertise, knowledge, and intuition to uncover unexpected issues and gain a deeper understanding of the product. By exploring the system without predefined test scripts, testers can simulate real-world user interactions and identify potential defects that may have been overlooked by scripted tests. Exploratory testing provides an invaluable perspective and complements other testing techniques by bringing a fresh and creative approach to uncovering system weaknesses.
Employing a combination of these testing techniques creates a holistic and comprehensive approach to software testing. By integrating usability testing, performance testing, security testing, boundary value analysis, equivalence partitioning, decision table testing, exploratory testing, and state transition testing into the testing strategy, organizations can ensure the delivery of high-quality software systems that meet user expectations, perform optimally, and provide a secure and reliable user experience.





